HIPAA-compliant push notifications: Build trust with encrypted messaging
More apps handle health data than ever before.
Even if you’re not a healthcare provider, your app might collect information that falls under HIPAA regulations.
Regular push notifications aren’t secure for this sensitive data. They travel as plain text through multiple servers, creating security and compliance risks.
Pushwoosh has been building push notification technology since 2014. We’ve recently achieved HIPAA compliance and know what it takes to implement proper encryption for sensitive messaging.
In this guide, we break down push notification encryption and show you how to implement it properly for both compliance and user engagement.
Why HIPAA compliance matters for push notifications
The Health Insurance Portability and Accountability Act (HIPAA) requires organizations to protect patient information.
This includes any data sent through push notifications, as they often contain sensitive details like appointment reminders, test results, and treatment updates.
Specifically, you need:
- Encryption for all health data in transit
- Access controls that limit who can send notifications
- Audit trails documenting when notifications are sent and to whom
- Proper handling of any data breach
Non-compliant push notifications create serious risks, including data breaches from intercepted messages, HIPAA violations with fines, damaged reputation, and potential lawsuits.
To mitigate these risks, the first line of defense is strong push notification encryption.
Push notification encryption explained
Push notification encryption is a security method that converts message content into a protected code that only the intended recipient can decode.
It shields sensitive information, such as health data, from unauthorized access. Unlike unencrypted messages, which can be intercepted and read in plain text.
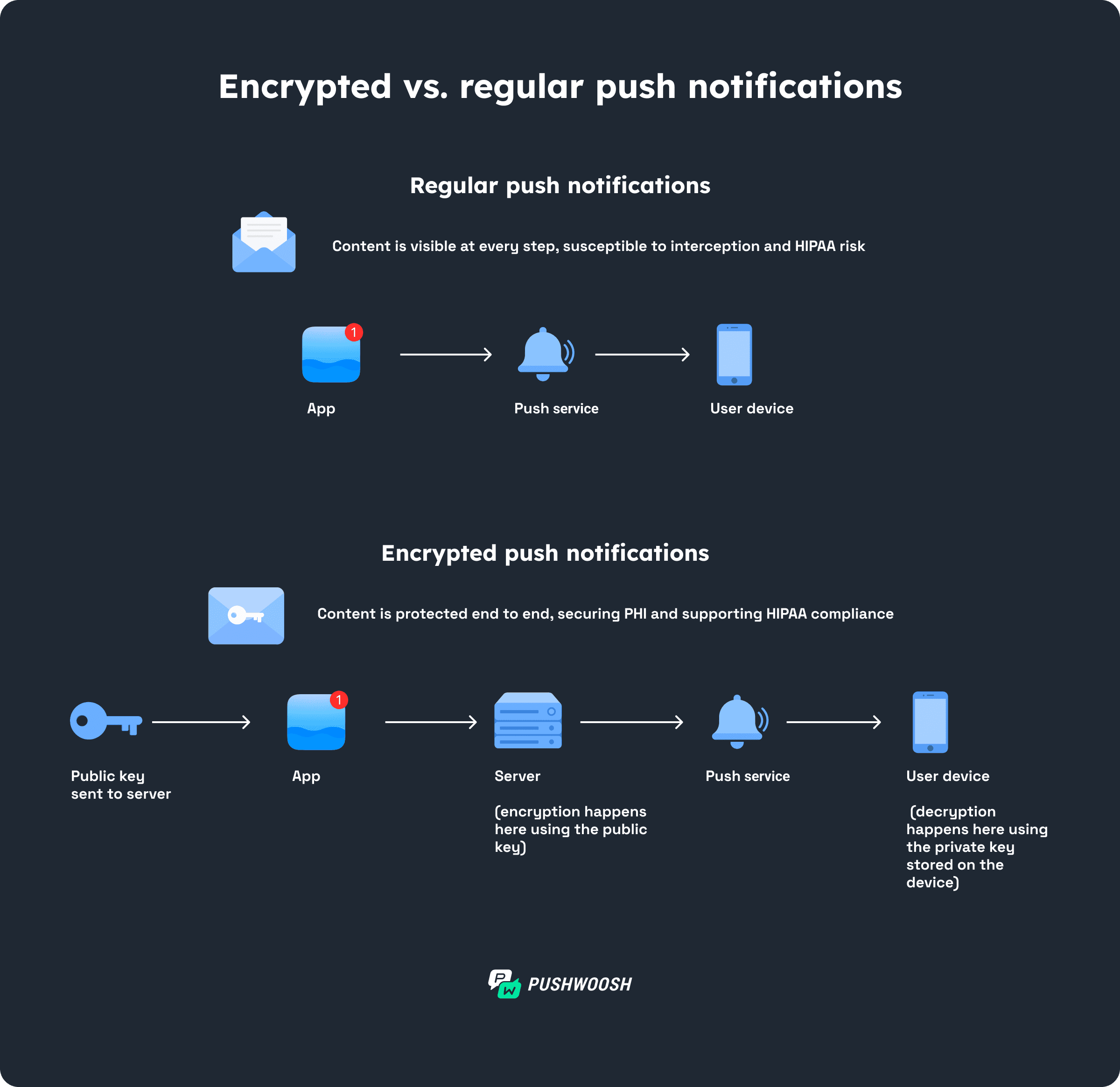
There are two key types of encryption for push notifications:
Encryption in transit uses TLS/SSL protocols to protect data while it moves between systems. This provides basic security but leaves content readable at each server it passes through.
End-to-end encryption protects data from sender to recipient. The message remains encrypted at every point in between, including Apple and Google’s servers.
However, HIPAA compliance goes beyond just encrypting messages.
You also need to protect encryption keys, restrict who can send health notifications, and keep records of all messaging activities.
Pushwoosh ensures all these security requirements through our HIPAA-compliant infrastructure.
Top use cases for encrypted notifications
Let’s go over the key examples of when encrypted push notifications are essential.
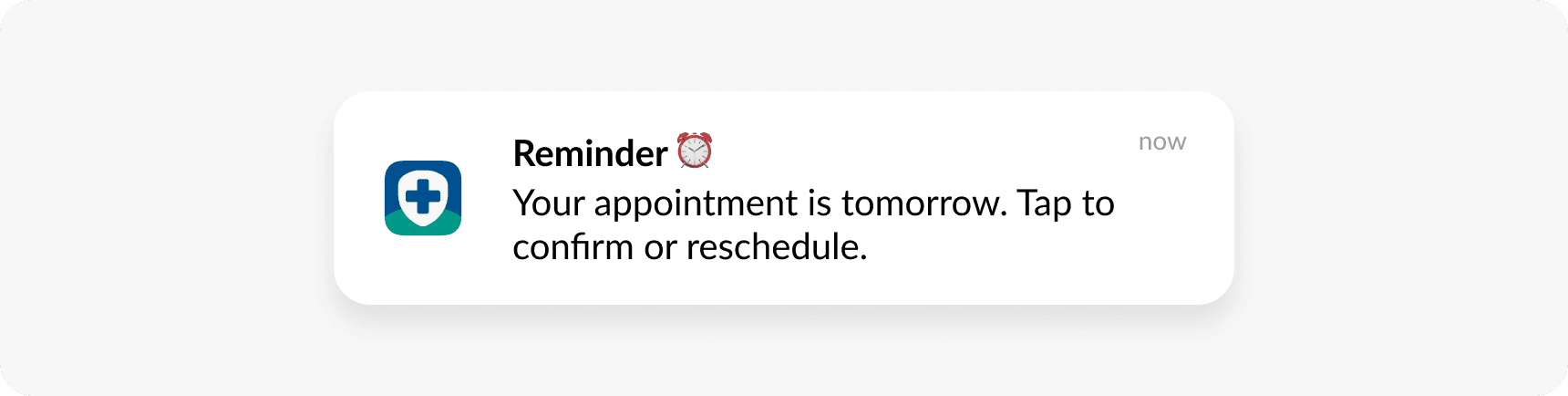
Appointment reminders
All push notifications for healthcare appointments must be encrypted, even when they contain minimal information, as mandated by HIPAA.
This is because they establish a documented connection between a patient and healthcare services, and typically include deep links to screens with detailed protected health information (PHI), such as provider details and medical history.
Lab result notifications
Notifications about test results also require encryption to protect patient identity and the fact that medical testing occurred (both of which are classified as PHI under HIPAA).
The deep links in these notifications connect to screens containing detailed health information.
Medication reminders
Medication alerts require encryption because they document patients’ sensitive information such as treatment status and medication schedule.
The notification itself confirms the patient is under active treatment, which is protected health information.
Telehealth session alerts
Virtual appointment reminders need encryption to protect patient identity and healthcare service utilization (both PHI elements).
These notifications confirm an ongoing treatment relationship that falls under HIPAA protection.
Provider updates
Communication notifications safeguard the patient-provider relationship and ensure continuity of care information. They also confirm that active medical care is being provided.
Wellness app notifications (when connected to healthcare)
For wellness apps that partner with healthcare providers or insurers, push notifications about health metrics or personalized insights must be encrypted in accordance with HIPAA.

☝️ Independent consumer apps aren’t legally required to encrypt, but doing so is advisable for user privacy and trust.
Mental health check-ins
Mood tracking reminders, therapy exercise prompts, and mental health insights contain sensitive information that deserves the same level of protection as physical health data.
Workplace health updates
Company apps that send alerts about health screenings, insurance benefits, or workplace health incidents need to secure any personally identifiable health information.
Fitness achievement updates (when part of healthcare programs)
When fitness apps partner with healthcare providers or insurers, even motivational notifications about steps, workouts, or health goals might require HIPAA-compliant delivery.
Key HIPAA requirements for push notifications
Encrypted push notifications are just one piece of the HIPAA compliance puzzle.
To properly protect patient data in your mobile communications, you need to address these five areas:
| Requirement category | What it means for push notifications |
|---|---|
| CIA triad: Confidentiality, integrity, availability | Keep your push notifications: Private: Only intended recipients can see them Accurate: Content stays unchanged during delivery Available: Messages get delivered reliably |
| Technical safeguards | Encrypt messages from start to finish Control who can send and receive sensitive notifications Keep records of all notification activity |
| Administrative safeguards | Have written rules for handling patient data Train your team on those rules Regularly check for security weaknesses |
| Physical safeguards | Protect the physical servers and computers Secure the locations where notification data is stored Safeguard devices used to send notifications |
| Business Associate Agreements (BAAs)—critical requirement | Require notification services to sign a Business Associate Agreement Hold vendors legally responsible for protecting patient data Protect yourself from liability if vendors mishandle information |
Pushwoosh: A HIPAA-compliant partner that goes above and beyond
Most messaging platforms weren’t built with data encryption as a priority.
Pushwoosh takes a different approach, offering:
HIPAA-certified security: Our platform has recently passed a comprehensive assessment by Riskpro India, validating our protection of patient data
End-to-end encryption: Sensitive information remains protected from creation to delivery using unbreakable RSA encryption
Omnichannel coverage: Secure messaging across push, in-app, email, SMS, WhatsApp, and Line
Easy implementation: Developer-friendly APIs and seamless integration with existing healthcare systems
Unlike regular notifications, Pushwoosh’s secure messaging uses a public-private key system where the private key never leaves the user’s device.
This ensures only the intended recipient can decrypt and read sensitive information. Even Apple and Google can’t access the content.
All this helps you achieve higher operational efficiency, improved patient adherence, lower total cost, and guaranteed message delivery even at high volumes.
For more information, please contact the Pushwoosh team.
FAQs
Are push notifications HIPAA-compliant by default?
No. Standard push notifications are sent as plain text that can be read by anyone with access to the transmission path, including Apple and Google’s servers. For HIPAA compliance, you need encrypted push notifications that protect sensitive health information throughout the entire delivery process. Learn more about data protection.
Does Pushwoosh offer encryption at rest?
Yes. Pushwoosh offers both encryption in transit and at rest. Our Encrypted Tags feature specifically allows you to store sensitive user attributes in an encrypted format within the Pushwoosh platform. This prevents unauthorized access to potentially sensitive information used for targeting or analytics purposes.
Can I send PHI in push messages?
Yes, but only with proper encryption. Pushwoosh’s secure push messaging uses end-to-end encryption with a public-private key system.
What kind of data does Pushwoosh collect?
Pushwoosh collects three types of data:
- Device data: Information like device model, OS version, and approximate location
- User data: Information that you choose to share with Pushwoosh (demographics, preferences)
- Event data: Actions users take in your app that you choose to track
How does Pushwoosh protect user data?
Pushwoosh protects user data through multiple security measures:
- End-to-end encryption using RSA encryption for secure messaging
- ISO 27001-certified data centers located in Germany
- GDPR compliance for data privacy protection
- Adherence to OWASP security principles
- HIPAA compliance verified by independent assessment
- Access controls limiting who can view and manage sensitive data
- Detailed activity logs for security monitoring and compliance verification